-
Notifications
You must be signed in to change notification settings - Fork 246
Usage
WEF must be run as root in order to launch.
It is also important to run WEF using Bash. Otherwise, it will not work.
Once you are inside the framework, all the functions and attacks are ready to be used.
You can type "help" in order to display a panel with different commands and their descriptions.
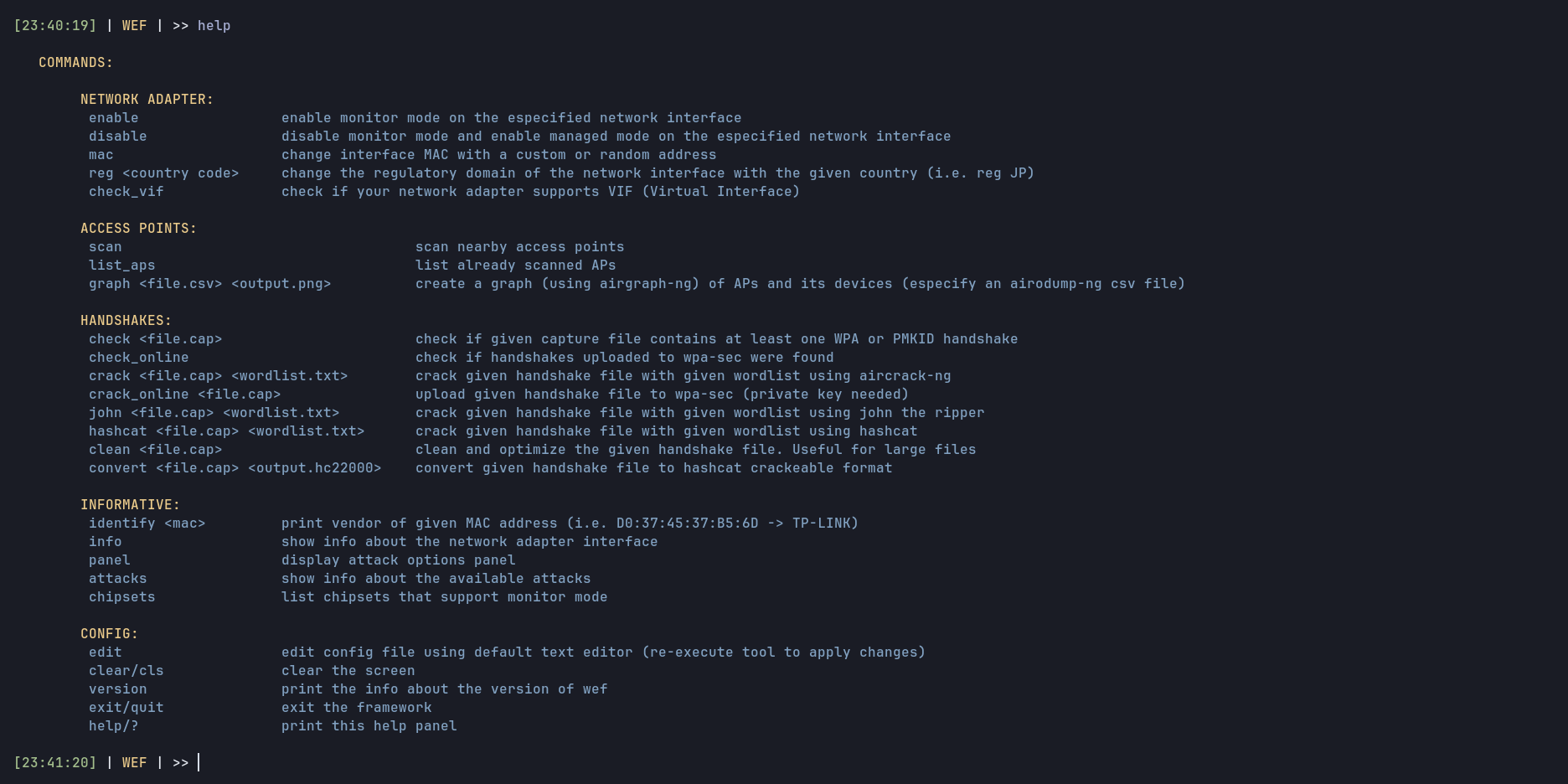
The most common usage of the tool would be:
- Enable monitor mode (
enablecommand if not already enabled automatically) - Select attack (i.e. deauth)
- Select target and set attack parameters
- Launch attack and see results
- Crack handshake (optional)
At the start of the program, WEF does some basic checks and gathers info (MAC address, interface name, current interface mode, frecuency bands and chipsets). If it is the very first time you execute WEF, then you will be prompted to create a configuration file that you will be able to edit later. When exiting the program, it checks the interface mode and other changes that has been made to revert them and cleaning everything, so that you do not have to worry.
You can select the different attacks by typing the number or typing the name of the attack. To perform the attacks, the interface should be in monitor mode, anyway the script detects the current mode so you will be notified.

The main purpose of this attack is obtaining the password of the target AP by using a rogue AP.
1 Rogue AP + Captive Portal
2 Rogue AP + Captive Portal + DoS
3 Rogue AP + Captive Portal + Wi-Fi Enterprise
4 Rogue AP + Captive Portal + Wi-Fi Enterprise + DoS
The second one is the most recommended to deploy, but also noiser since it deauthenticates connected devices. It will ask you to configure the features and capabilities of the rogue AP: using custom or built-in templates, verifying or not the captured passwords (handshake needed), spoofing target's BSSID, and enabling KARMA mode (hostapd-wpe). Afterwards, it will proceed to set all the things up using hostapd, dnsmasq, lighttpd and aireplay-ng.
Once the windows have launched, you can simply check if there was any error by looking at their output. The hostapd window should say "AP-ENABLED" suggesting that the AP has been created. The dnsmasq window should not indicate any major error. The lighttpd window should simply report that the web server has started. The aireplay-ng window (if you chose DoS) should be sending the deauthentication frames until you decide to stop the attack. Finally the last window is simply checking constantly the devices connected and displaying the password attempts.

If you have chosen any of the options that uses DoS, as the legit network is being attacked and users cannot connect to it, they will see the fake AP with the same name (even same BSSID if you enable BSSID spoofing), they will connect to it and probably provide the password of the legitimate on a simple but effective fake router login. Captive portal templates were taken (and slightly modified) from airgeddon so all credits to v1s1t0r1sh3r3 and his awesome project.